ADAPT Framework for Modelling Adversary Behaviour
Hey everyone,
Today I will share my thoughts on one of our industry’s favourite terms: Advanced Persistent Threats.
In the infosec circles, APT has been a buzzword for quite some time, usually pointing to cyber intrusions backed by nation-states. But in my opinion, this term is far from useful. For instance, what does “Advanced” mean exactly? We see lots of reports labelling attacks as “advanced” or “sophisticated” without really defining what that entails. The truth is, many of these so-called APT intrusions aren’t all that advanced. They’re often just good at adapting their tactics and being OPSEC aware.
Let’s take a look at the decision chart provided below, which presents the most detailed criteria for identifying APTs I have seen to date.
Note that many of the questions in the chart require assessments rather than straightforward facts to be answered. For example:
Is the Group Nation-State Sponsored?
Does the Group Engage in Long-Term Intelligence Gathering?
Does the Group Exhibit a High Degree of Organisational Sophistication?
This complexity in classifying something as an ‘APT’ tends to make the process unnecessarily complex, without offering much add-value for those defending against these threats.
This blogpost will propose a more accurate way to talk about adversaries, which I call ADAPT. It stands for Advanced, Adaptive, Persistent, and Targeted. Let’s break it down.
1. Advanced
In our field, it is a tendency to slap the label “advanced” on nearly every cyber threat. But if everything is advanced, then really, nothing is. “Advanced” here should mean something specific: those really high-end, costly capabilities that only a few adversaries can get their hands on. We’re talking about less than 1% of all cyber attacks. Examples include:
Commercial Spyware (e.g: Pegasus)
Zero-day exploits
ICS-tailored Malware
Deep packet inspection and similar ISP-level attacks
So one may look at the capabilities employed in an intrusion set, and if either of the above capabilities are present, then we can speak about an Advanced adversary.
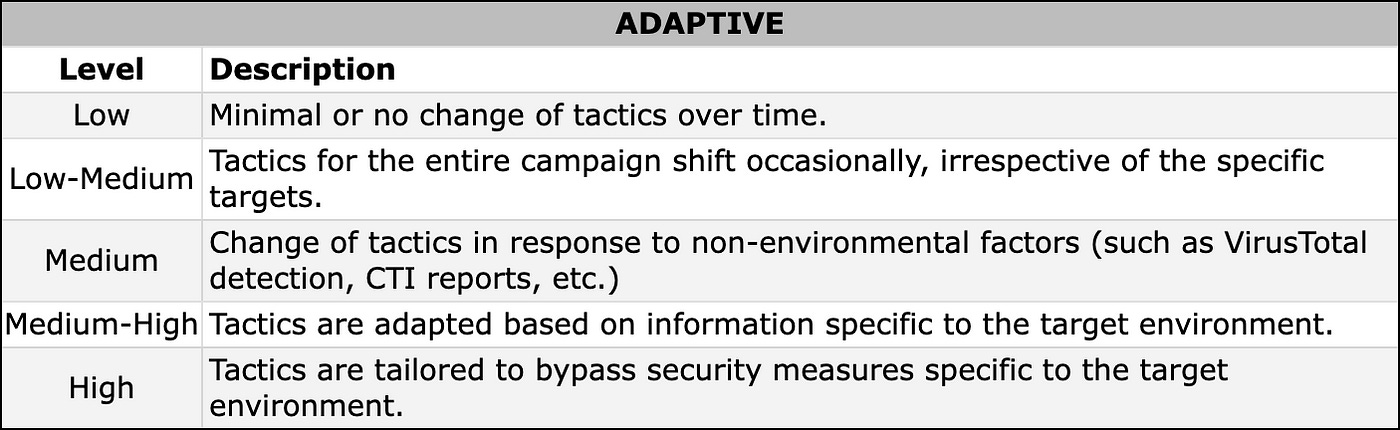
2. Adaptive
This trait reflects an adversary’s willingness to modify tactics in response to environmental changes. Adaptiveness often correlates with high-precision targeting. In targeted campaigns, adversaries typically engage in target-specific information gathering and tailor their tactics accordingly. Conversely, opportunistic campaigns tend to use a similar set of tools across numerous targets simultaneously. Adaptiveness is a spectrum rather than a binary value, and it can vary across different phases of an intrusion.
3. Persistent
Persistence is the adversary’s dedication to continue their attacks until achieving their objective. While sometimes related to adaptiveness or high-precision targeting, persistence can manifest independently as well. For example, the Leery Turtle[*] campaigns during the period of 2017–2020 exhibited high persistence but little tactical variation over time. Thus, it’s more useful to assess this trait separately, on a spectrum.
4. Targeted
As implied, this property indicates the specificity of targeted individuals or entities during an intrusion. According to ProofPoint, over 95% of APT campaigns target no more than five customers at a time. Despite challenges in assessment due to collection gaps, understanding the targeted nature of an attack can be insightful. This property should also be viewed as a spectrum, from low-precision to high-precision.
Mapping ADAPT to Defense Strategies
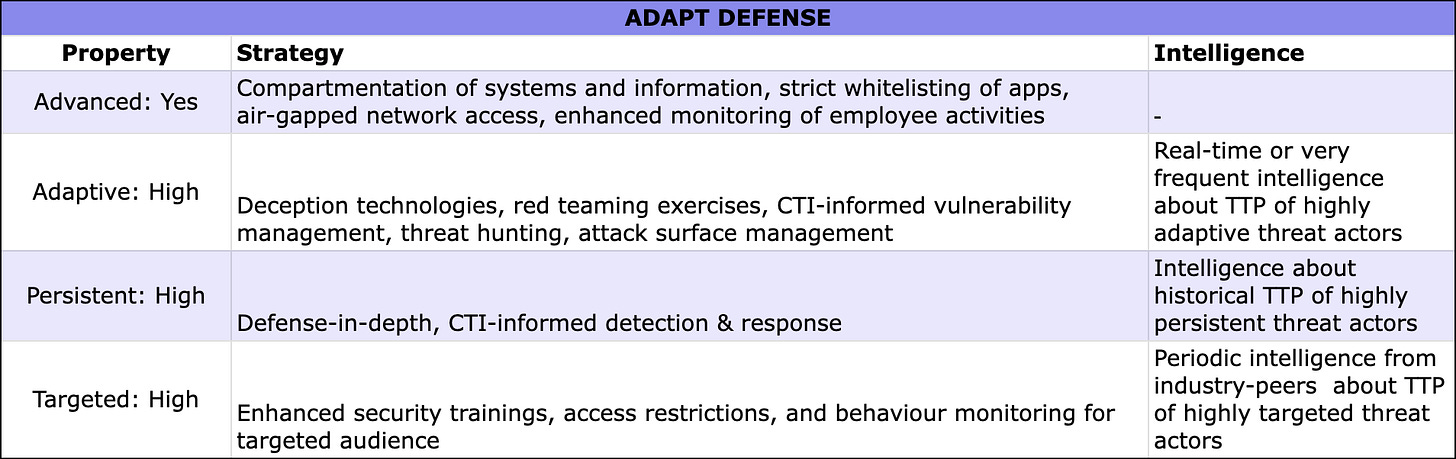
The ADAPT framework is very useful for cyber defense planning.
Using ADAPT with Adversary Persona Cards
We can integrate ADAPT properties into Adversary Persona Cards and assign ratings to each attribute to calculate an overall ADAPT Score. This allows ADAPT to be used as an additional factor in prioritising different types of adversaries, with a higher ADAPT Score signifying a more difficult adversary to defend against.
Strategising for High-End ADAPT Properties
ADAPT also allows tailored strategies for mitigating threats at the higher end of each property. Defense planners can ask the following questions to initiate a brainstorming:
How can we defend ourselves against an adversary with advanced (0-day, DPI etc.) capabilities?
How can we defend ourselves against an adversary who is highly adaptive to our environment?
How can we defend ourselves against an adversary who is very persistent?
How can we defend ourselves against an adversary who is very selective in its targets?
Assigning ADAPT to Threat Actor Profiles
Lastly, similar to the first approach, ADAPT can also be applied to threat actor profiles. It’s very straightforward to assign ADAPT values by examining the facts related to an intrusion set.
Let’s take the following example of HAFNIUM:
ADVANCED: YES (4 pts) — MSTIC. (2021, March 2). HAFNIUM targeting Exchange Servers with 0-day exploits.
ADAPTIVE: HIGH (4 pts) — Usage of 0days, targeted nature of the attacks, target-specific information gathering (T1592.004, T1589.002, T1590), and internal discovery (T1057, T1018, T1016, T1033)
PERSISTENT: HIGH (4 pts) — Threat group is known to be operating since at least 2021 with a perceived objective of intelligence collection.
TARGETED: MEDIUM-HIGH (3 pts) — HAFNIUM primarily targets entities in the US across a number of industry sectors, including infectious disease researchers, law firms, higher education institutions, defense contractors, policy think tanks, and NGOs.
HAFNIUM’s ADAPT Score: 15 / 16
Another example of Leery Turtle:
ADVANCED: NO (0 pts) — No observed usage of advanced capabilities.
ADAPTIVE: MEDIUM (2 pts) — Change of tactics in response to public CTI reports.
PERSISTENT: HIGH (4 pts) — Campaigns have been ongoing from at least 2017 up to the 2023.
TARGETED: MEDIUM-HIGH (3 pts) — Cryptocurrency exchanges are targeted worldwide.
Leery Turtle’s ADAPT Score: 9 / 16
Conclusion
Using ADAPT gives us a clearer picture of cyber adversary behaviour. Understanding these four aspects — Advanced, Adaptive, Persistent, and Targeted — helps us better gauge the strength and strategies of our cyber defences. Ultimately, ADAPT is intended to provide a framework to guide cybersecurity efforts in a more targeted and effective manner.
I hope you found this article useful. See you in the next one!