Lessons from the Nucor and Thyssenkrupp Breaches
What the Nucor and Thyssenkrupp breaches reveal about cyber conflict
The influence of geopolitics on cyber events continues to grow, especially as critical industries are increasingly targeted. The breaches at Nucor (May 2025) and Thyssenkrupp (early 2024) are recent examples that show just how exposed key economic sectors are. Attribution is still complicated, as always, but the downstream economic impact is clear. Even the perception of a supply shortage in some industries can lead to price fluctuations, triggering a trickle-down effect throughout the entire economy. These types of attacks are not rare in the context of geopolitical conflicts, where cyber operations are used to punish countries for supporting the opposing side.
The Nucor Incident: A Disruption of Critical Industry
In May 2025, Nucor Corporation, the largest steel producer in the U.S., fell victim to a cyberattack that led to a temporary halt in operations across several of its plants. [1] The breach, which appears to have been a ransomware attack, disrupted production lines and forced the company to take critical IT infrastructure offline to contain the damage.
As a foundational player in steel production, Nucor supports a wide range of downstream industries, including construction, automotive, and defense. Disrupting steel manufacturing has a cascade effect: not only does it delay supply chains, but it also impacts pricing and availability across national and global markets. In macroeconomic terms, even the perception of supply instability in materials as central as steel can lead to price fluctuations and broader market volatility.
The Thyssenkrupp Incident: A Parallel in Europe
In early 2024, German steel manufacturer Thyssenkrupp experienced a cyberattack that disrupted its automotive division, halting production at multiple facilities. [2] Although operational continuity was restored relatively quickly, the breach demonstrated similar systemic fragilities. As with Nucor, the attackers targeted a company that is central to its country's industrial capacity.
Thyssenkrupp’s role in Germany parallels that of Nucor in the U.S. Both firms represent critical nodes in their respective national economies. While there is no public attribution connecting these two incidents, their similar timing, scale, and strategic impact raise important questions. Particularly when examined within the context of ongoing geopolitical tensions.
Geopolitical Context: A Pattern Emerges
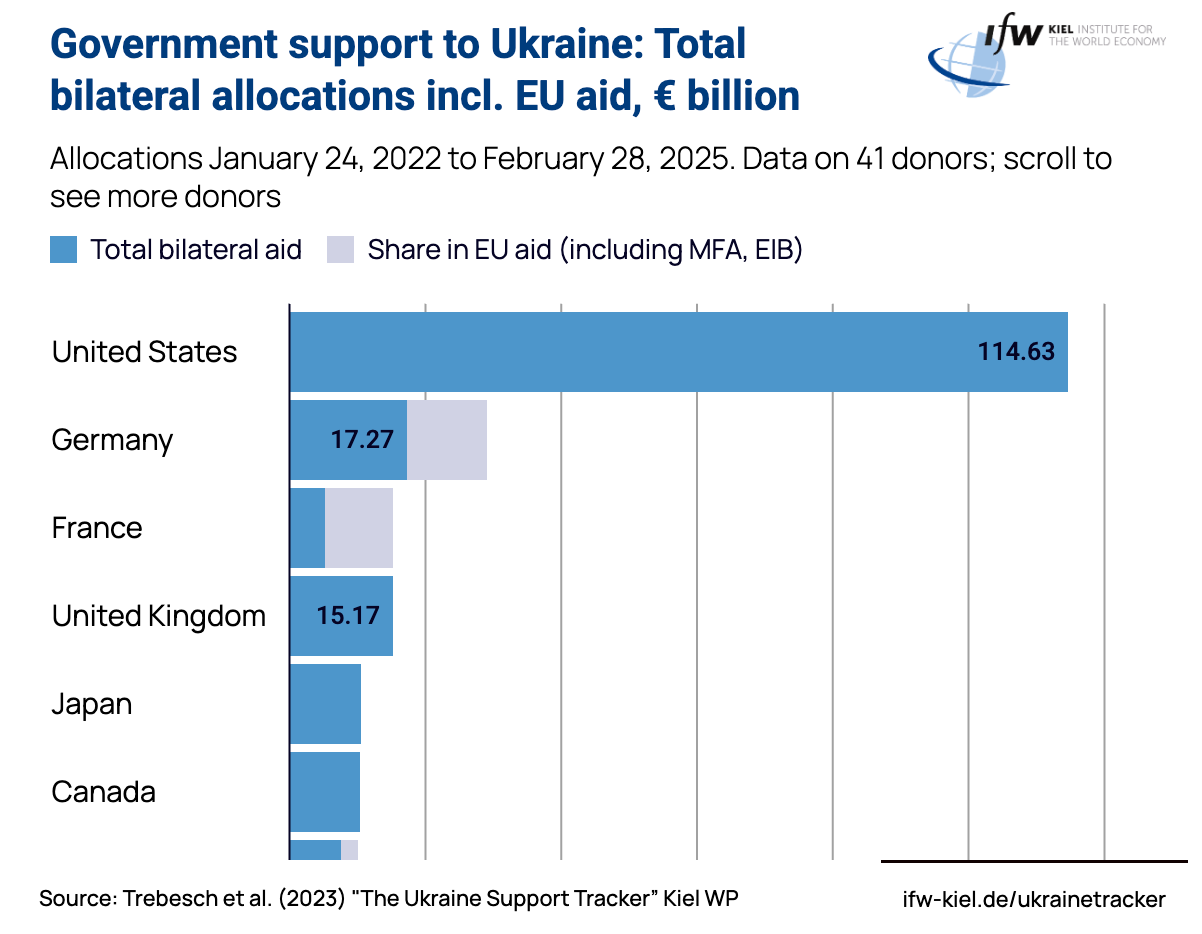
According to the Ukraine Support Tracker by the Kiel Institute, the United States and Germany are the top two contributors of military, financial, and humanitarian aid to Ukraine. [3] Germany, notably, is both the leading EU-level contributor and the largest individual contributor within the EU overall. The U.S. has also maintained the highest total level of assistance globally.
Concurrently, Kaspersky’s Q1 2024 ICS report shows that U.S. and German industries are the top two most-targeted globally in terms of industrial cybersecurity incidents. [4] This correlation between leading aid contributions and a surge in attacks on their industrial bases may not be coincidental.
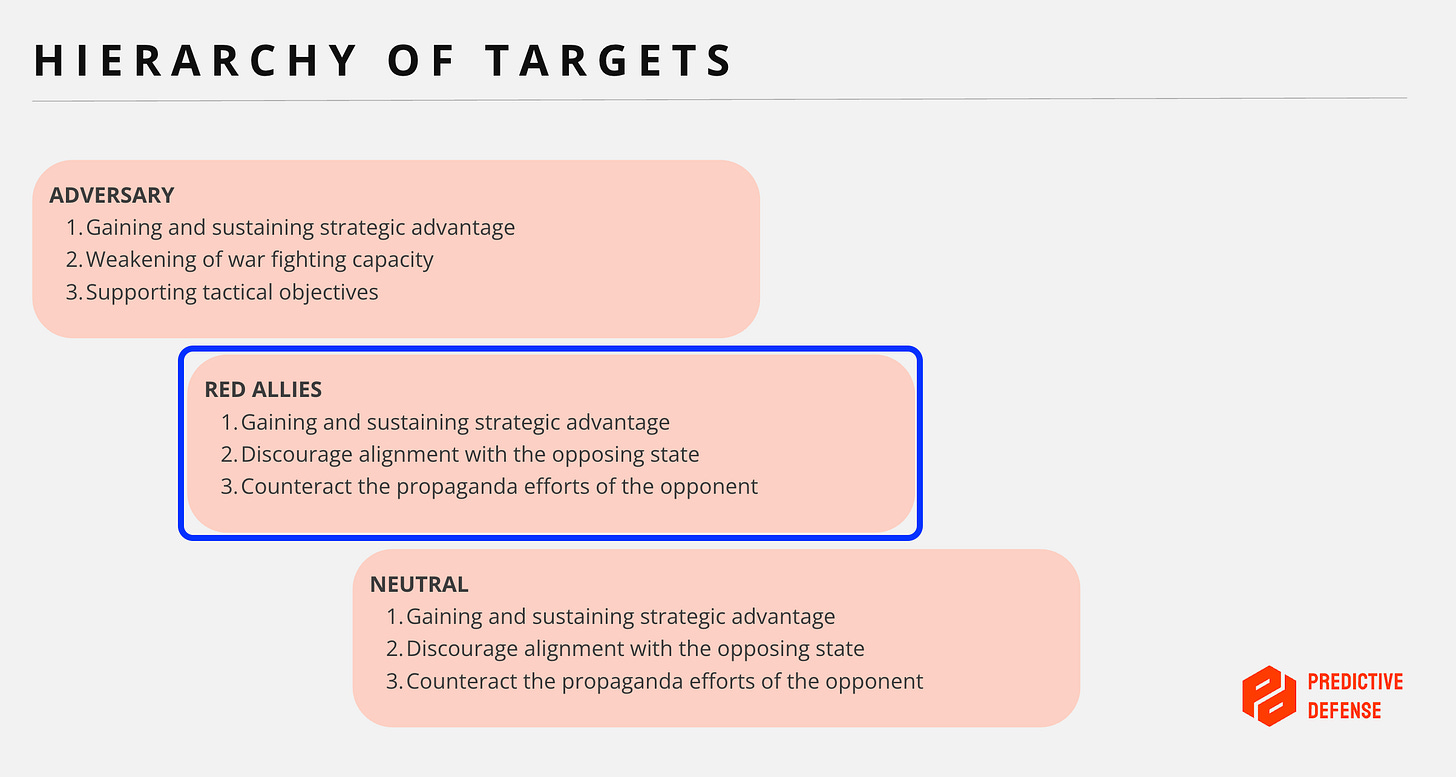
While no direct attribution can be made, it is reasonable to assess the possibility that these attacks form part of a broader effort to exert economic and political pressure on the so-called "Red Allies": those nations seen as supporting Ukraine from the perspective of Russian strategic interest. Disrupting their domestic industries could serve to undermine public support, strain logistics, and signal a capability for retaliatory escalation.
OT-Centric Cyber Operations as Strategic Tools
Dragos' 2025 OT Cybersecurity report highlights the increased frequency of OT-centric cyber operations, particularly in countries involved in high-stakes geopolitical alignments. It notes that “KAMACITE and ELECTRUM continue to collaborate in support of Russian military objectives by targeting critical infrastructure in Ukraine.” [5]
Attacks on companies like Nucor and Thyssenkrupp fit this pattern. They do not aim for direct military advantage but seek instead to disrupt economic infrastructure as a potent form of coercion. Strategic OT disruptions can constrain infrastructure projects, and degrade economic resilience.
From a military operations perspective, these operations align well with the concept of countervalue targeting, where the objective is not battlefield dominance but the degradation of assets critical to national morale and function. [6] This contrasts with counterforce strategies that target military capabilities directly.
Moreover, analysis methods like ASCOPE/PMESII can help anticipate where such attacks might occur. The IPB/IPOE process emphasizes understanding the adversary's centers of gravity for the most economic use of force. [7] In this light, Nucor and Thyssenkrupp could be seen as predictable targets due to their central roles in national infrastructure.
These campaigns may aim not just to degrade supply chains but to control narrative. Causing domestic concern, triggering economic ripple effects, and ultimately deterring future alignment or support for Ukraine. If you’re interested in this type of analysis, feel free to check out our post below.
Curious About More? Join Our Workshop
I will be leading a specialized Geopolitical Cyber Threat Intelligence Workshop on 21–22 June 2025, designed for cybersecurity professionals, CTI analysts, and cyber risk teams looking to understand how geopolitical tensions translate into cyber threats.
This two-day, instructor-led workshop focuses on the role of cyber operations in advancing political, economic, and military objectives. Drawing on real-world conflicts and intelligence methodologies, the course offers a structured approach to geopolitical threat analysis, strategic foresight, and cyber risk forecasting.