Predictive Defense: How to do cyber crime forecasting with examples
Hi everyone,
In this article, we will examine how to do forecasts on financially motivated cyber crime with examples. If you haven’t read my previous article on this topic yet, I recommend reading it: Trend Forecasting - How to spot the next big thing in cyber crime?
Before delving into the methodology, let’s examine the basic dynamics of the cyber crime economy.
Understanding the profit dynamics
The methods through which criminals can profit can be classified into four main groups.
Selling of commodities: Criminals may attempt to sell acquired goods such as customer databases, premium accounts, coupon codes, credit cards, bank accounts, or sensitive documents. This provides a quick way for attackers to make money with less risk, especially when there is high demand for the goods.
Exploitation of computing resources: Sometimes, criminals can leverage the processing power of compromised systems. This can generate a reasonable income with a sufficiently large botnet. Examples include clicking on ads, generating fake video views/app downloads, creating website traffic, boosting social media followers, and the most notable, cryptocurrency mining.
Extortion: Criminals may attempt to extort companies by launching DDoS attacks, encrypting files with ransomware, or threatening to release sensitive data that could lead to reputational damage, regulatory fines, and more.
Providing services (tertiary sector): While a campaign itself may appear technically simple and straightforward, the process from preparation to cashing out can be lengthy and complex. Recognising this, some criminals offer services that facilitate various aspects of cyberattacks to other hackers. This is the most diverse market, with examples including advertising, malvertising, affiliate services, credit card checkers, cash-out and shipping services, cryptocurrency laundering, bulletproof hosting, encryptors, hash crackers, ready-to-use toolkits, DDoS-as-a-service, initial access brokers, and 2FA bypass services.
Changes in Market Conditions
Within the context of the profit-making methods we have listed above, consumer demand plays a pivotal role, and when demand can be met by at least one provider, it gives rise to a market. The driving force behind all markets is demand, and thus, meaningful changes in supply cannot be expected without significant changes in demand. Therefore, it is crucial to monitor changes in supply & demand and understand the factors influencing these changes. The factors we will list shortly are interrelated, and a change in one often triggers changes in several others.
Possible causes of change in supply & demand
Changes in consumer habits: Consumer habits sometimes change independently of the cybercrime ecosystem and can positively or negatively impact demand for a product. Particularly in markets targeting end-users, such as premium accounts and coupon codes, consumer habits directly influence the market’s size. For instance, the COVID-19 pandemic worldwide shifted consumers towards digital products and services independently of the cybercrime ecosystem. As a natural consequence, demand for products like premium accounts and coupon codes increased, triggering market growth. A future example could be, in case demand for NFTs continues to rise and NFT trading becomes a part of our daily lives, we can expect the emergence of a market for NFT art theft.
Changes in the value of commodities: The value of a commodity can increase or decrease independently of the cybercrime ecosystem, and this has ramifications in the cybercrime economy. A striking example is the significant increase in the value of cryptocurrencies when they entered our daily lives, leading to the emergence of cryptocurrency-related attacks such as cryptominer botnets and cryptojacking. If the value of cryptocurrencies were to drop to a level where these attacks are no longer financially viable, we might no longer see such attacks. Significant increases in commodity values often lead to an increase in supply as more individuals seek to profit from the higher profit margins they offer.
Expanding Target Range: The internet comprises a vast array of technological platforms, each of which presents potential opportunities for criminals. In their pursuit of increased profits, criminals expand their target base as far as their capabilities allow, often jumping onto different platforms. For example, the shift of various end-user applications, especially banking, to mobile platforms has naturally led attackers to target mobile platforms. This has been evident in the shift from traditional credit card fraud methods to mobile banking malware. The targeting of IoT devices by botnets and the extension of cryptominer attacks to cloud platforms are other examples. The desire of criminals to broaden their target range creates a natural demand for products and services in this direction. As the target range expands, the number of products entering the market, meaning the supply, increases.
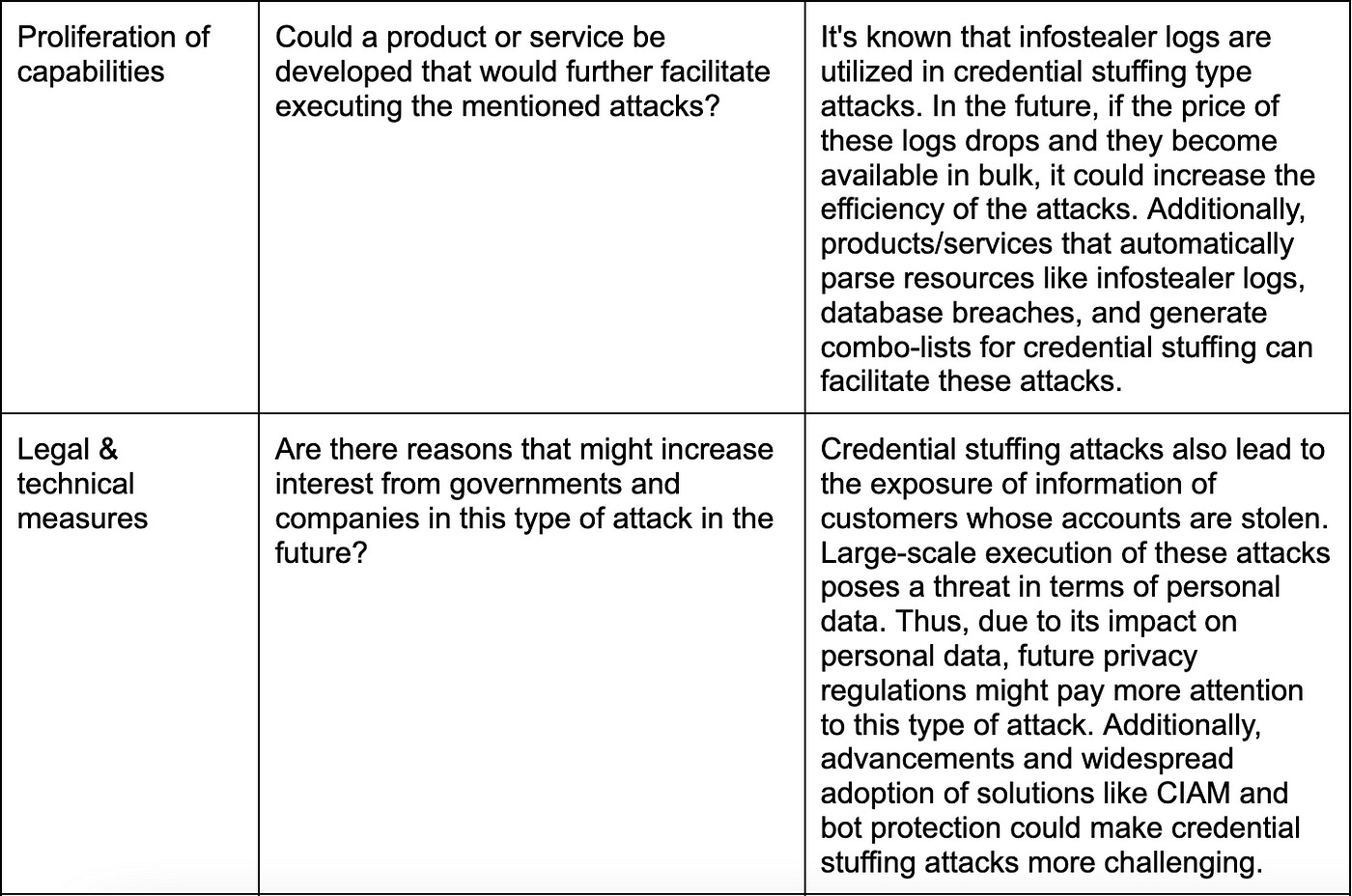
Proliferation of capabilities: Some attack methods are not executable by everyone due to the technical knowledge they require. In case a way can be developed to decouple a technique’s execution from its user, it results in the proliferation of attack capabilities, making what was previously a complex attack chain accessible to a wider audience. This decoupling sometimes occurs through the development of automated tools. Examples include exploit kits, phishing kits, botnet panels, etc. Sometimes, multi-step or technically complex attack types are offered to consumers as “managed services”. Ransomware-as-a-service, scanning-as-a-service, malware distribution services, stresser services, and the like fall into this category. This scenario increases the number of players in a market, thereby increasing supply, but an excessive proliferation of capabilities can lead to market saturation.
Legal and technical measures: The increase in legal and technical measures against a particular type of cybercrime can both hinder its execution and reduce its profitability. For example, legal regulations developed against credit card fraud made banks responsible for customer protection and liable for compensating customers for losses due to fraud. Consequently, banks developed new technical measures against credit card fraud, making it more difficult to convert stolen credit card funds into cash. As a result, these technical measures made the task more costly and challenging for attackers. Such changes typically affect supply rather than demand since they increase the cost of executing the attack.
Law enforcement pressure: At times, law enforcement agencies focus on specific types of crimes and prioritise capturing the individuals involved. This naturally creates pressure on those committing the targeted crimes. The aim here is to make the targeted crime riskier, thereby deterring criminals. Over time, law enforcement priorities can change, leading to varying degrees of pressure on different markets. Sometimes, law enforcement operations can shut down significant avenues of trade or disable a few major suppliers in a market, resulting in a temporary decrease in supply.
How does the market respond to changing market conditions?
Past experiences show that as a result of changing market conditions, there can be three types of outcomes: innovation, migration, consolidation and expansion.
Innovation
At times, while the demand for a product or service does not decrease, the market can shrink due to any pressure on supply. For example, supply might temporarily decrease because a technical measure makes an attack more difficult. In such cases, criminals first try to overcome whatever is causing the pressure on supply. Sometimes, criminals develop a new method to bypass existing technical measures, which is called technical innovation. At other times, criminals change the ways to make money from the same product, and this is referred to as market innovation. Features like the “pre-order” option introduced in some markets where Infostealer logs are sold, or dark web forums starting to sell forum messages through a paid API, are examples of market innovation.
Migration
If the demand for a product or service significantly decreases or disappears, we usually observe the actors serving in that market migrating to more profitable markets. In rarer cases, these actors can create new markets by developing a market innovation.
Consolidation
When the cost of an attack significantly increases or the attack becomes too risky, we see that the market consolidates in the hands of the major players. For example, as it became harder to convert stolen credit card information into cash, it necessitated the development of new methods. Following this, we observed that the credit card market consolidated into the hands of a minority group familiar with these new methods. This minority group, knowledgeable in cashing out the stolen credit cards, started to buy credit card data in bulk. This demand encouraged those who stole credit card data to sell their data in bulk to these actors instead of trying to cash them out on their own. As a result, the market consolidated.
Expansion
Changes causing an expanding target range and proliferation of capabilities can increase the profit margin of that type of attack. This situation leads to more actors entering the market, resulting in the market’s expansion.
How to do forecasting step-by-step
Step 1: Choose a market and conduct basic market research
Based on the types of threats relevant to your organization, identify markets of interest. Then, using the parameters mentioned above, conduct research to gain insights into the current state of the market. The following questions, which I’ve listed for basic market research, might help guide your inquiry.
Intelligence Requirements for Basic Market Research:
How many successful trades have been conducted within a certain time frame, if applicable?
What’s the estimated trade volume within a certain time frame, if applicable?
Who are the regular suppliers, if relevant?
Who are the primary buyers, if relevant?
What is the nature of the relationship between these individuals, showcased in a relationship matrix?
As an example, let’s take a look at the market for selling premium accounts/coupon codes, which is closely related to credential stuffing attacks. The research doesn’t necessarily need to provide completely accurate results, especially regarding market volume and the number of transactions. What’s essential is to have insights into market distribution, operational methods, and the relationships among the actors.
Premium Account/Coupon Code Market Research
Step 2: Assess Possible Changes in Defined Conditions
List the market drivers we outlined in the earlier sections of the article for your target market. Then, considering the current situation, speculate on potential changes in any of these parameters.
Potential Changes in Premium Account/Coupon Code Market Conditions
Step 3: Brainstorm Scenarios for Potential Outcomes
In this third step, we’ll use a method called the ‘cone of plausibility’ to brainstorm how the market might respond to the changes we listed in the previous section. While brainstorming, we’ll also consider the patterns of innovation, consolidation, expansion, and migration that we discussed in earlier sections.
Scenarios in response to changing market conditions:
Criminals will find a way to circumvent the CIAM and bot protections, and continue their attacks as usual. (innovation)
The profit margin for attacks substantially increases due to decreased infostealer log prices, leading to more players entering the market. (expansion)
With their source of income diminishing due to decreased customer demand, criminals migrate to other markets, such as initial access brokerage, where they can repurpose their skills. (migration)
Due to the increasing difficulty of exploitation, the market will consolidate around a few players with high capabilities. (consolidation)
Criminals will abandon the credential stuffing technique and shift their focus to exploiting application vulnerabilities for account takeover. (innovation)
Step 4: Determine Early Indicators to Monitor Scenario Emergence
In this final step, for every scenario we anticipate, we will hypothesise how we might observe its emergence and create a list of early signs to monitor. Our assumption is that changes observed in these indicators will reflect the transformations we expect in the market. For instance, in the case study we examined, we could use the indicators listed below as early signs.
However, it’s essential to note that these signs may not always support the assumed hypothesis. Therefore, testing these assumptions analytically and trying to validate or refute them using available data, wherever possible, is crucial.
For instance, in the chart below, coupon sales and initial access sales are compared. Observations indicate a trend that began in 2023 and reversed in April. However, this shift in trend does not necessarily imply that those involved in credential stuffing have migrated to the initial access market. After observing such a trend change, a more in-depth investigation should be conducted to determine whether the two events are genuinely related.
If it turns out that the two events are unrelated, then our assumption is incorrect, and this event can no longer be used as an indicator.
Ok.. so what? — Assess and prepare for impacts on your security strategy
Changes in cybercrime markets, as mentioned, could lead to outcomes such as certain types of attacks becoming more or less frequent in the future or the sophistication level of the techniques used in the attacks increasing. Incorporating these kinds of forecasts into defense planning can better position organizations against potential future threats. Companies can leverage these predictions to prioritize their security investments. Or, they can establish prerequisites to respond more effectively to anticipated threats (e.g., enhancing inter-departmental collaboration, developing incident response plans, conducting drills, etc.). Moreover, forecasting how the market might evolve can facilitate refining intelligence gathering objectives and pre-positioning them. By doing so, we can transition from a security approach that merely responds to the present to one that anticipates and positions itself for the future.
I hope you’ve enjoyed reading. Until next time!